Scams for Outlook
Create your own blogspot.com because blogger shares last a very short time.
| Identifier |
The id is your "secret key", to access the data data. |
Hack Outlook
How to hack Outlook and Hotmail in 2026, step by step
Learn to Hack Hotmail
Using phishing, you can hack any Outlook email account. This is because this method targets the largest vulnerabilities. If you want to learn more about this, follow these steps:
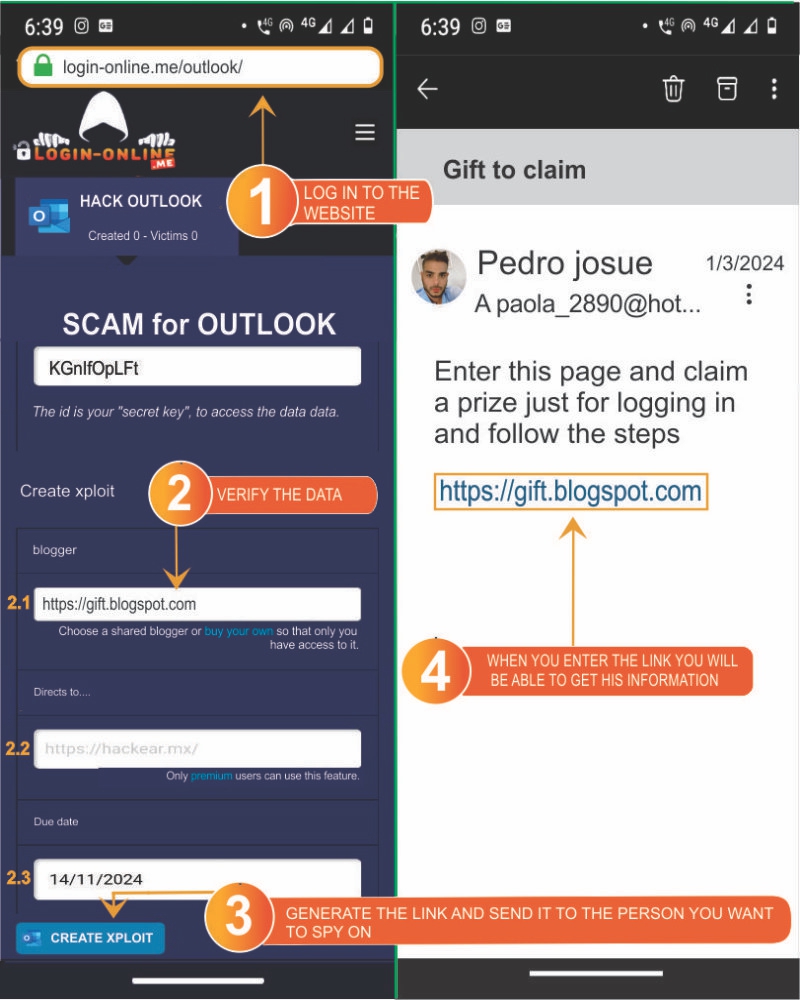
- 1️⃣ Visit the website login-online.me.
- Save the identifier, as this code allows you to access the data obtained with SCAM. However, it is recommended to register with an email.
- 2️⃣ Choose the page or social network for which you want to create SCAM. In this case, it would be XPOLITS OUTLOOK.
- 2️⃣.1️⃣ Enter the link of a movie, song, or photo; this is what your victim will see in the end. This feature is only available to premium users.
- 2️⃣.2️⃣ Redirect to a YouTube video so that your victim does not suspect anything.
- 2️⃣.3️⃣ Select the expiration date for the SCAM.
- 3️⃣ Click "Create SCAM."
- 4️⃣ Send the link to the people whose data you want to steal.
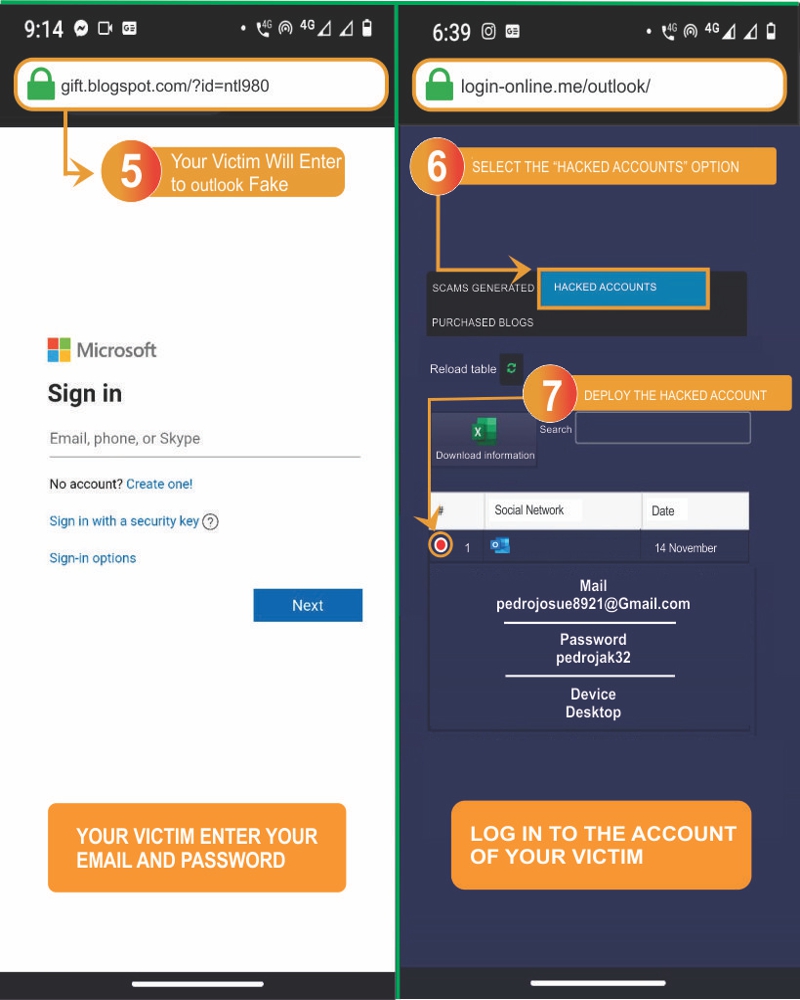
- 5️⃣ Wait for the person to fall for the trick and log in using their credentials on the fake Outlook page.
- 6️⃣ Once the victim has fallen, navigate to Hacked Accounts.
- 7️⃣ Finally, you can see their email, password, and even their IP address.
Login-online.me is a platform that allows you to store usernames and passwords for any type of social network or site, such as Hotmail. The platform has a system that simulates the login page of websites like Hotmail, Instagram, Facebook, Twitter, Skype, among others. It can steal login credentials by making someone believe they are logging into an official website, when in reality, it is not.
You need to find a way to send the person you want to hack the link to the fake page generated after creating the SCAM. Once the person logs into the fake Hotmail page, their login credentials will be stored on Login-online.me.
Advantages:
- You can access the person's account instantly, and they will never know you have their credentials.
- You don’t need to be a professional hacker; you only need to bait them and watch as they fall for it.
- You can keep track of SCAMs and create multiple links at once.
- It is a free tool, so you won’t need to download annoying applications.
Disadvantages:
- Hacking Outlook using SCAM can be risky, as you might get caught.
- Some browsers, like Chrome, warn users that the SCAM is dangerous.
- If the person discovers the trick, they might report you.
- To enjoy more benefits, you need to pay for the premium version.
How to Find the Obtained Data
While on login-online.me:
- 🔍 Go to the top of the page.
- 📂 Look for the section labeled "HACKED ACCOUNTS."
- 📜 A list of hacked accounts will be displayed.
If this person doesn’t live with you or lives far away, you can use the excuse that you're participating in a competition (it can be any type). You can ask them to vote for you by logging into Hotmail through that link. With this excuse, even if the person notices the link is not the official Hotmail URL, they will likely believe what you're saying and won’t realize the scam.
However, if you're looking for another way to hack Outlook, you can tell the future victim that you need to send an email to someone who doesn’t have Facebook, WhatsApp, or Instagram. Or tell them that the person told you they only wanted to contact you via Outlook. If they ask about your Outlook account, you can say that you forgot the password and have no way of recovering it.
When your victim enters their email and password, all you have to do is log into their account.
How to Protect Yourself from Phishing?
As you have already seen, it is very easy for someone to access your Outlook account without your permission. This can leave you vulnerable. Our recommendation is to follow these tips:
- • Do not click on suspicious links: Make sure the link is exactly the same as the original.
- • Be wary of suspicious emails: Hackers often try to impersonate companies.
- • Enable two-step verification: This security measure ensures that even if someone has your email and password, they still can’t access your account.
- • Install antivirus on your device: Antivirus programs like Kaspersky or ESET provide anti-phishing tools.
- • Verify the authenticity of the message: Check the message text, profile image, email or phone number, and the way the message is written.
How to Hack Hotmail Using a Keylogger

Keylogger is an app that records everything typed on the phone or device. Once the person logs into Hotmail (Outlook), the data will be saved in the Keylogger app without the victim realizing. Then, you’ll need to open the app and search based on the date and time the person logged in to find the saved data.
It's important to warn you about a small flaw in Keylogger. This app will only save passwords and email addresses if the victim enables the “show password” option when typing it. Therefore, if this option is not enabled when the password is entered, only the dots that protect the password will be saved.
So, you must find a way to activate this option before giving your phone to the person you want to log into Hotmail from your mobile. If you're okay with this, then visit the page at keylogger.
How to Hack Hotmail Using a Keylogger
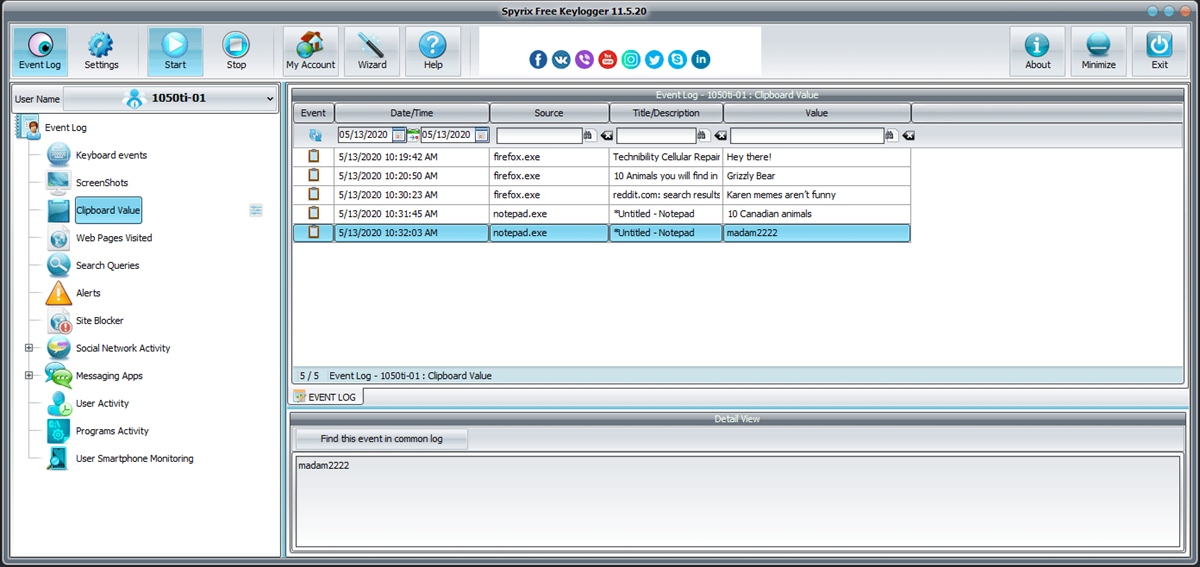
Keylogger is an app that records everything typed on the phone or device. Once the person logs into Hotmail (Outlook), the data will be saved in the Keylogger app without the victim realizing. Then, you’ll need to open the app and search based on the date and time the person logged in to find the saved data.
It's important to warn you about a small flaw in Keylogger. This app will only save passwords and email addresses if the victim enables the “show password” option when typing it. Therefore, if this option is not enabled when the password is entered, only the dots that protect the password will be saved.
So, you must find a way to activate this option before giving your phone to the person you want to log into Hotmail from your mobile. If you're okay with this, then visit the page at keylogger.
Contact Us!
If you still have questions about our tool, you can contact us via WhatsApp or TikTok.
Send message on WhatsApp
























