Scams for Twitter
Create your own blogspot.com because blogger shares last a very short time.
| Identifier |
The id is your "secret key", to access the data data. |
How to hack a Twitter account
How to hack Twitter: Step by Step
If you're interested in hacking a Twitter account, whether to find out what your partner, friend, or family member is hiding, you've come to the right place. Follow the step-by-step guide on how to hack Twitter for free in just a few minutes using the scam method..
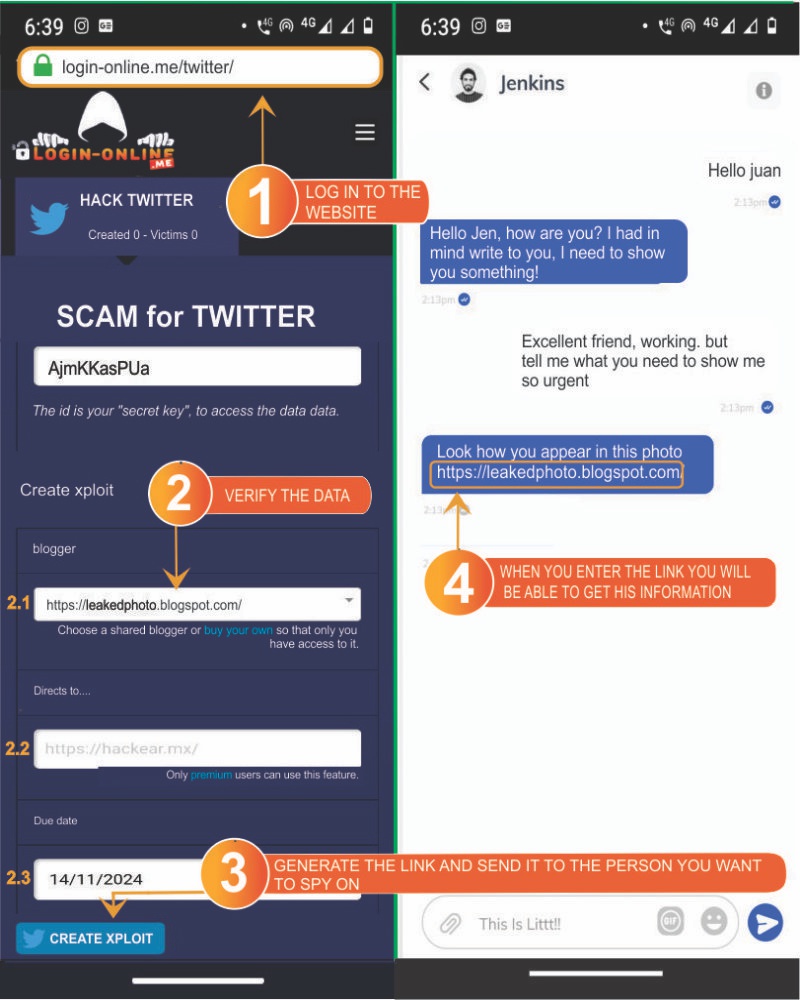
- 1️⃣ Go to the website https://Login-online.me/twitter
-
2️⃣ Verify the data:
make sure everything is set up correctly.
- 2️⃣.1️⃣ Select a Blogger from the available options. This cannot be modified; you can only choose from the available options.
- 2️⃣.2️⃣ Choose the page to which the link will redirect after obtaining the data.
- 2️⃣.3️⃣ Select an expiration date; the link will work until the chosen date.
- 3️⃣ Click on the button "Create Twitter SCAM" and wait for the link to be generated: a link will appear that you can send to your victim with the Twitter clone. Remember to send it along with a message to act as bait.
- 4️⃣ Return to the website Login-online.me to check the captured data: once the victim enters their email and password on the fake page, you will be able to review them.
-
If you cannot trick your target, don't worry, you can always try again using another social engineering technique.
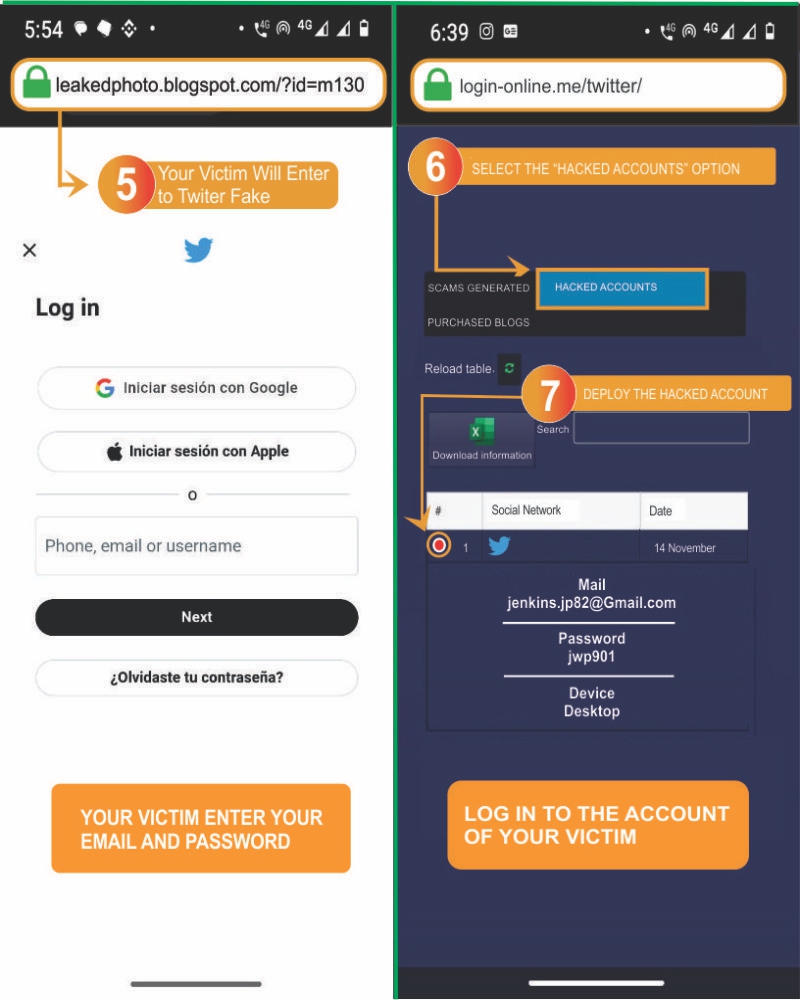
- 5️⃣ Your victim will access the fake Twitter: they will believe it is the original page and enter their email and password without hesitation.
- 6️⃣ Return to Login-online.me: go to the "Hacked Accounts" section to retrieve the password.
- 7️⃣ View the hacked accounts: now you only need to log into your victim's account.
When your victim logs into the fake page believing it is the original Twitter platform, you will be able to see their access details in "Obtained Data" on Login-online.me
How to hack Twitter with Scam?
Victim
Last seen online: 3:17 PM
Hey, hi friend, how are you?
12:30 PMGood, thank you, and you?
12:32 PMThat's great! Hey, there's something I want to show you...
12:35 PMI don't know if you've seen it yet, but I think they're talking about you on Twitter twitter.blogspot.com/?id=145d203f
12:36 PMSeriously?? Is it who I think it is?? Let me check it right away...
12:37 PMThrough our Twitter account hacking tool, you can set up a scam in just minutes. But then what? The most important part: making the victim visit the fake page created from Login-es.com and entering their details.
If you followed the previous step-by-step guide on how to hack a Twitter account, you should have created a custom scam link for your victim. If you visit it, you'll see a page that looks identical to Twitter's login, but with one difference: when the victim enters their details, they’ll be saved for you to view.
You need to consider two important things when wanting to hack a Twitter account. The first is the redirection link you entered when creating the scam, as that will be where the victim is sent after entering their login details. If you use a non-existent tweet link or a random tweet link, it may cause the victim to suspect they have been hacked.
The second important consideration is the message you’ll use to send the link to the victim. This is where your creativity comes in. You can follow the example we provided, creating concern or curiosity about a tweet you just saw, or you can impersonate the official Twitter platform through an email requesting additional account information.
What is a scam and what is it for?
A Twitter Xploit consists of a fake page that simulates the official one. In this way, you can obtain the login details entered by the victim, such as the username and password. You just need to be convincing and trick your victim into logging in from the link.

SCAMs consist of fake pages that temporarily impersonate an official page, such as Twitter. In this way, we can obtain the entered data, such as the username and password. You just need to be convincing and trick your victim into logging in from the link.
It is one of the easiest methods to hack Twitter to use. You don't need technical computer knowledge to hack a Twitter account.
SCAMs work in a very simple way:
- Thanks to our page, a fake Twitter link is created.
- Accompany the SCAM with social engineering, which involves a bait message to trick the victim.
- If social engineering is done correctly, the SCAM software will do its job, storing and compromising the data so that you can access the account without issues.
It is important to accompany the link with an attractive message that encourages the user to log in. Otherwise, the method won't be very effective.
What does Login-online.me offer?
Hack Twitter 2025 Online, Free and Easy with our Scam creation tool is now very simple. We offer you the possibility to create deceptive links with our step-by-step guide.
From Login-online.me you can use this hacking tool completely for free. Create your own Twitter Xploit right now!
Do you have any questions? Contact us through our WhatsApp at any time, 7 days a week.
Advantages and Disadvantages of Hacking Twitter with SCAM
Advantages:
- ✔️ Quickly obtain all the information and conversations of the people you're interested in.
- ✔️ You don't need to be a hacker. Anyone can use our method to hack Twitter for free.
- ✔️ Allows you to keep track of the SCAM and create more than one link.
- ✔️ It's a completely free method, so you won't have to pay anything to use it. Additionally, you can hack Twitter without any app.
Disadvantages:
- ❌ Risk of being discovered: Hacking a Twitter account with SCAM always carries the fear of being detected.
- ❌ Links detected as fake: Sometimes, links generated with SCAM may be flagged as fraudulent, reducing their effectiveness.
- ❌ Repetition of the process: If the victim realizes the hacking attempt, you will have to restart the entire procedure.
Contact Us!
If you still have questions about our tool, you can contact us via WhatsApp.
Send message via WhatsApp



























