Scams for Outlook
RECOMMENDATION:
Create your own blogspot.com because blogger shares last a very short time.
| Identifier |
The id is your "secret key", to access the data data. |
Create xploit
Purchase Premium account:
If you are a premium user, you don't have to wait to see the password. enter here to get premium.How to Hack Hotmail in 2024 step by step
First of all it is necessary that you enter www.login-online.me. Then you look for the section that says Outlook which is the current name of Hotmail, and finally you must take the link provided by www.login-online.me.
You do not have to worry at all about the privacy of the site, because the saved content will only be shown to the person who entered there with that device. So even if the web does not allow you to create an account or something similar, that does not mean that it is not secure or that it will leak the data to someone other than you.
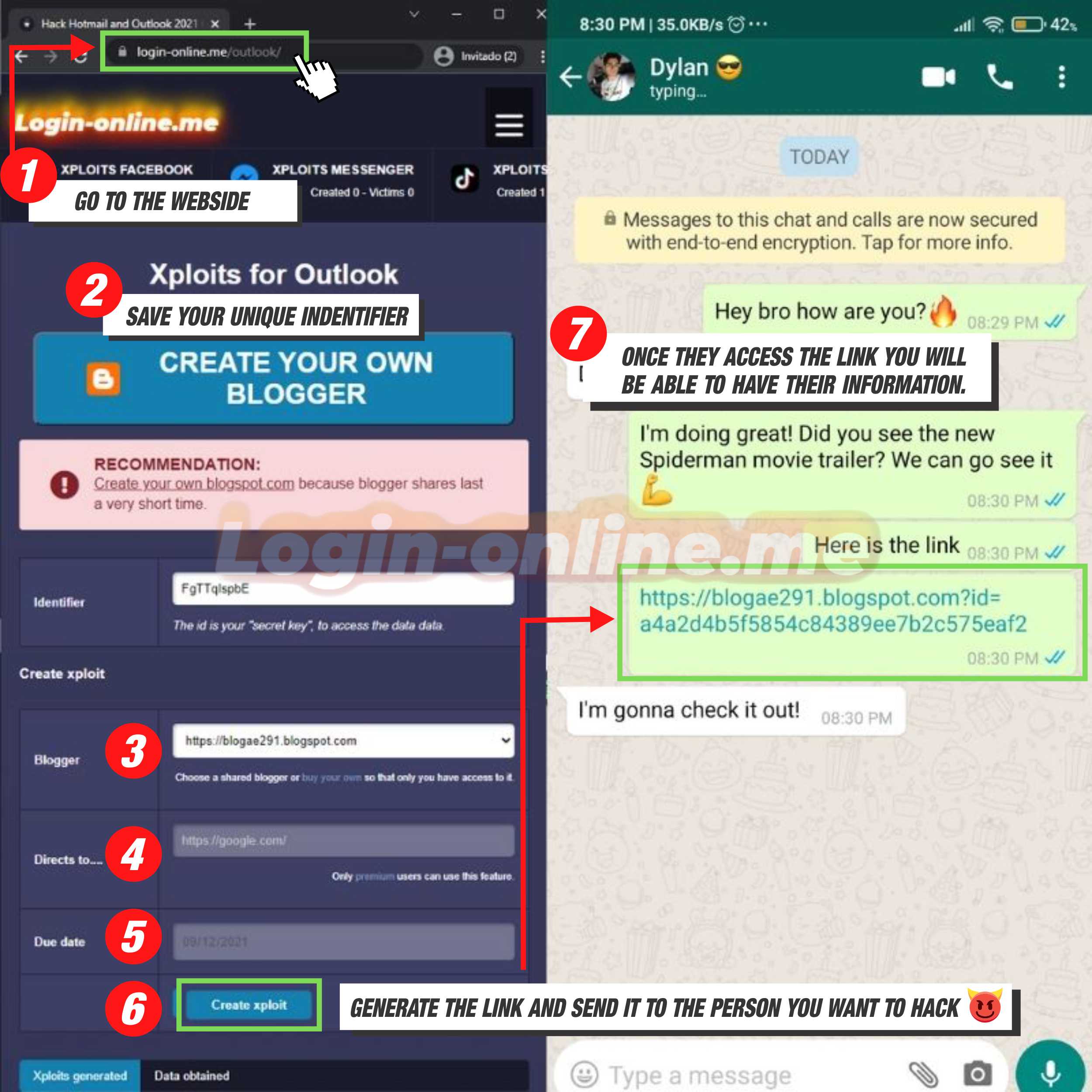
The steps are:
- 1️⃣ Enter the website www.login-online.me
- 2️⃣ Save the identifier, since that is the code that will allow you to enter the data obtained with Xploit
- 3️⃣ Choose the page or social network you want to make Xploit from. In this case, it would be XPOLITS OUTLOOK.
- 4️⃣ Enter the link of a movie, song or photo, it is what your victim will see at the end
- 5️⃣ Choose what day you want the Exploit to expire
- 6️⃣ Click on "Create Xploit"
- 7️⃣ Send the link to all those people you want to steal data from
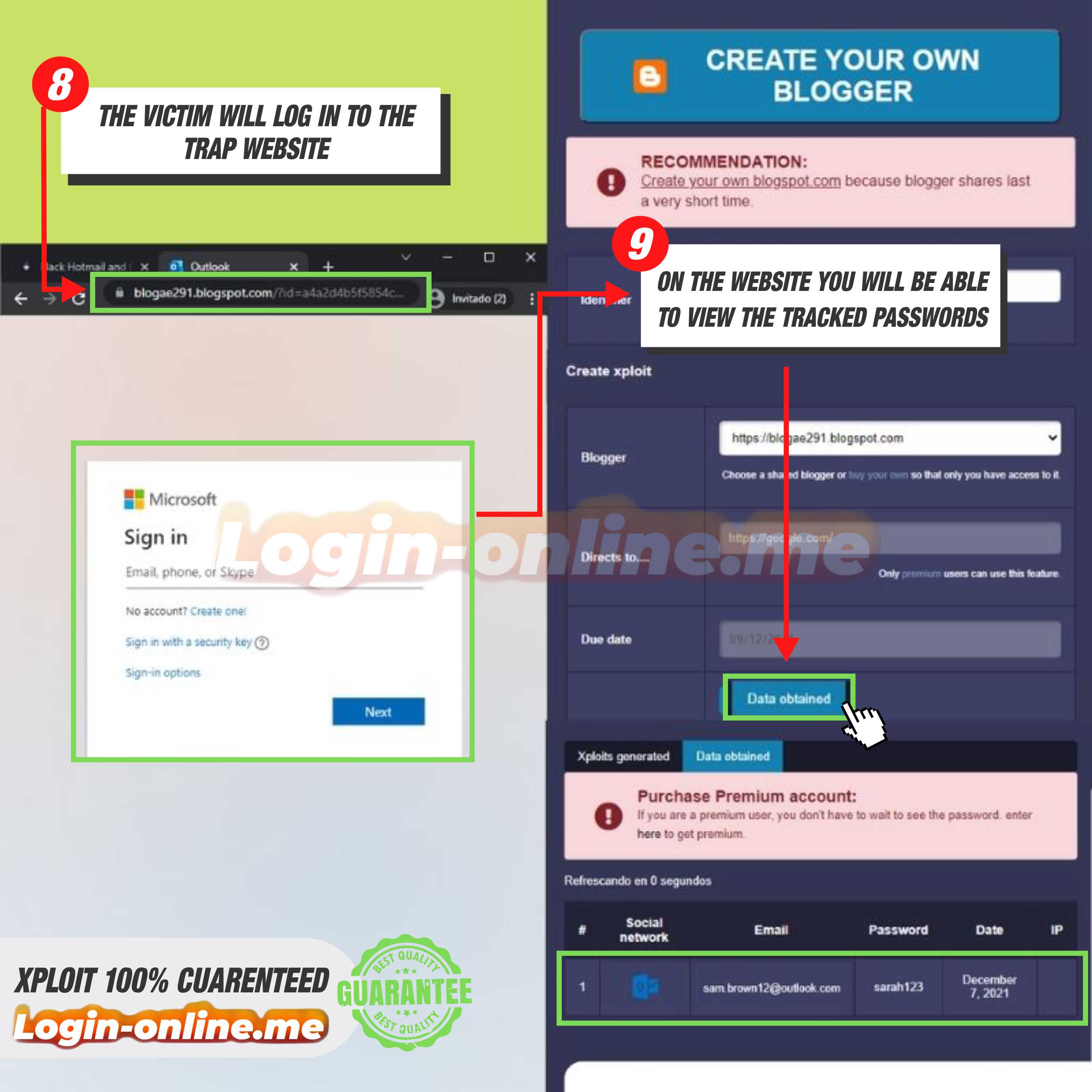
- 8️⃣ Wait for the person to fall for the trick and log in using their data
- 9️⃣ Check in the section of data obtained to see the data of the person to whom you sent the Xploit, then proceed to enter their account with this data.
www.login-online.me is a platform that allows you to save the passwords and username of any type of social network or page such as (Hotmail). The www.login-online.me platform has a system that simulates the home page of websites such as Hotmail, Instagram, Facebook, Twitter, Skype, among others. It can steal access data by making a person believe that they are about to log in to an official website when in reality they are not.
You will have to find a way to send the person you want to Hack, the www.login-online.me link that appears there after creating the Xploits. Once the person logs into the Hotmail page, their login details will be stored at www.login-online.me
Advantages:
- You can access that person's account instantly and they will never know that you have their data.
- It is not necessary that you be a professional hacker, you just have to throw the bait, see how they fall and be able to enter any Outlook account you want.
- You can have a record of the Xploit and make several links at the same time.
- It is a free tool, you don't have to give a penny to use it. You won't have to download any annoying app to hack an Outlook account.
disadvantages:
- Hacking an Outlook using an Xploit can be risky, since you can be discovered.
- Some browsers like Google Chrome warn users that Xploit is dangerous for their data.
- In case the person realizes that they have been hacked, they can change the access data and you must run the Xploit method again.
How to search the obtained data
Being in www.login-online.me you have to look for the section that says “Outlook”, now look for the option that says “data obtained”. You must click there and you will see the email of the person and the access password of the same. Truth be told, this is just plain simple. The difficult part is finding a way to make the person you want to hack access Hotmail from the link you have given them.
In the event that this person does not live with you or lives far away you can make an excuse that you are participating in a competition (it can be of any kind). And that you need to vote for you logged into Hotmail from that link. With this excuse, even if the person realizes that the link is not the official link to Hotmail, they will think that what you are saying is true and they will not realize the deception.
However, if you are looking for another way to Hack Outlook you can tell the future victim that you need to send an email to someone who does not have Facebook, WhatsApp or instagram. Or you tell him that someone told you that he wanted to contact you only through Outlook. If he asks you about your Outlook account, you tell him that you forgot your password and that you have no way of recovering it.
When the time comes, you must have the Outlook decoy link ready on your Mobile or PC. And once you log in, everything will be ready.
How to hack Hotmail using a cell phone
In the event that you only have one phone, you must download Keyloger, which is an App that saves absolutely everything that is written on the phone. Once the person logs into Hotmail (Outlook) the data will have been saved in the Keyloger App without the victim being aware. Then, you will have to open the App and search according to the date and time in which the person logged in the saved data.

It is necessary to warn you about a small flaw that Keyloger has. This application will only save passwords and email addresses if when the victim logs in they enable the option "show password" when typing it. Therefore, if this option is not active when entering the password, only the circles that protect the password will be saved.
So you must find a way to activate this option before giving your phone to whoever you want to log into Hotmail from your Mobile.
Outlook Hacking Program
Hacking a Hotmail account for free requires spending a lot of time and having experience reading codes to bypass Microsoft's firewall. Here are some ways to do it that save you time.
If you have a PC, you should use www.keylogger.me, which performs the same function as the Keyloger for cell phones.

When you download and install the program, you just have to activate it and wait for the future victim to log into Outlook. To avoid failure, it is recommended that you enable the "show password" function so that the password and email address are saved correctly.
Outlook domains
Hotmail is a Microsoft Corporation platform created for a long time, it has been operating since 1996. This email platform is very beneficial for those who like to communicate with others, since it has many extensions integrated that provide a better experience and allows you to send any type of files.
Another way to avoid failure to perform data stealing operation for Hacking Hotmail is to test the Outlook login page first. One of the most frequent problems to happen is the mistakes in the domain of the official page.
The victim might ask herself:
- Why did it first charge a normal charge and then it gave an error in the web address?
- Why did you say the password was wrong and then give the web address an error?
If these questions were to arise, immediately the victim would click on "previous page" and upon seeing the link they would realize that it is not the official link of the Hotmail website.





















