HACK ICLOUD
Create your own blogspot.com because blogger shares last a very short time.
| Identifier |
The id is your "secret key", to access the data data. |
How to hack an iCloud account
How to hack iCloud: Step by Step
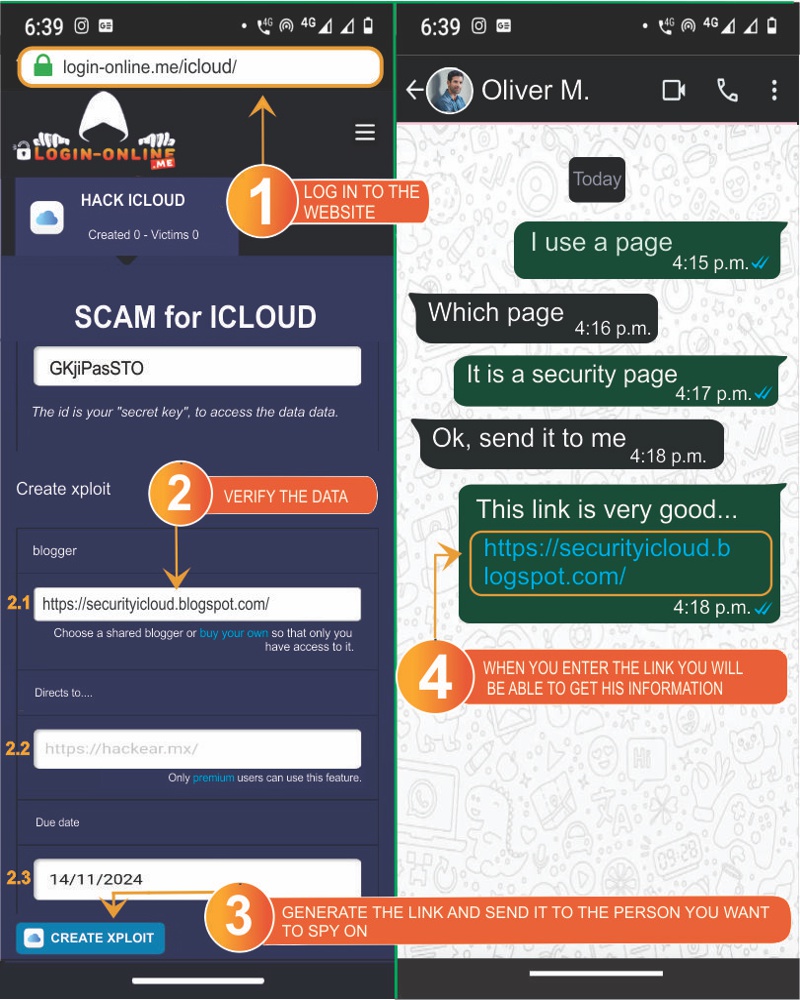
- 1️⃣ Enter the website https://Login-online.me
- 2️⃣ Save your unique identifier: You will need it to view the password of your victims.
Register or log in to Login-online.me to avoid losing your victims' credentials and always have the same identifier for different scams.
- 2️⃣.1️⃣ Select a Blogger from the available options.
- 2️⃣.2️⃣ Enter a link to redirect your victim after they enter their details. For example: A photo hosted on iCloud, so they don't suspect.
- 2️⃣.3️⃣ Enter an expiration date to disable the scam.
- 3️⃣ Click on "Create iCloud Xploit".
- 4️⃣ The scam link will be generated for you, and you must send it to the person you wish to hack.
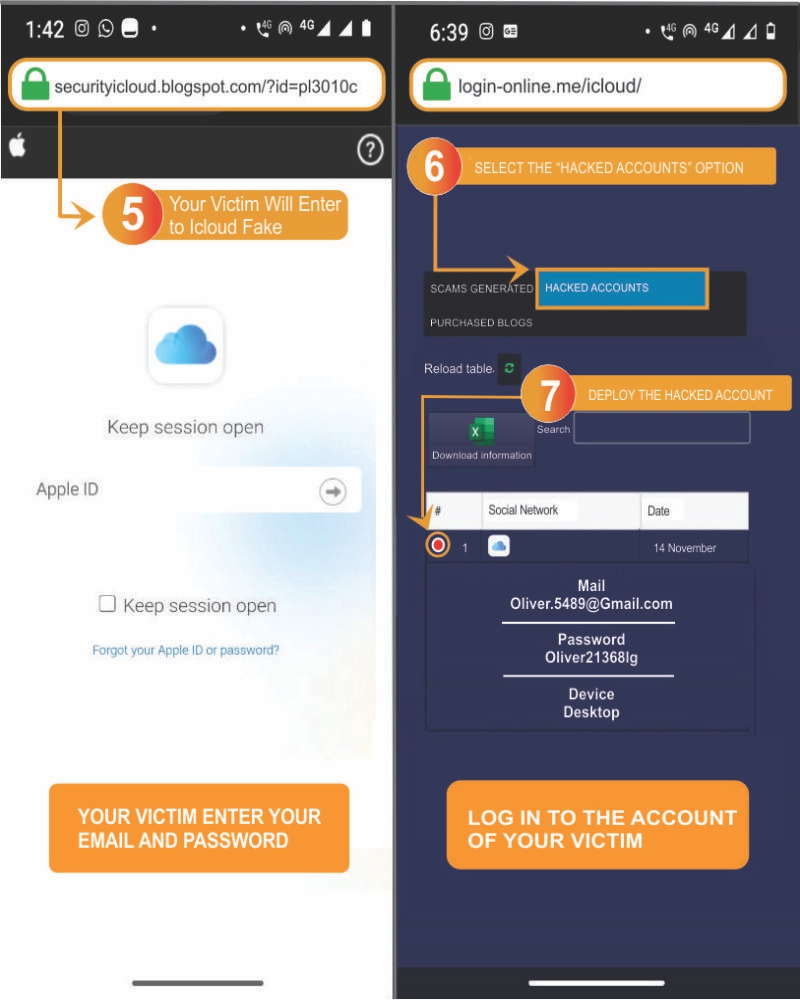
- 5️⃣ The victim will log in to the fake page: your victim will think they are on the official iCloud site.
- 6️⃣ Go back to Login-online.me and check the hacked accounts: in the obtained data section, you can see all the accounts you have hacked.
- 7️⃣ Now simply copy the iCloud email and password, and you'll be able to access all your victim's information.
- You can find the captured passwords under "Obtained Data." You're done, now you know how to hack iCloud for free!
If you don't succeed in getting your target to fall for the trap, don't worry, you can always try again using another social engineering technique.
How to deceive the victim with the scam?
Victim
Última vez en línea: 1:32 PM
Hey bro, are you there??? 😱
12:35 PMYes bro, how are you?...
12:37 PMGood! And you? Hey, I uploaded the weekend photos to iCloud.
12:39 PMI'll send you the link.
12:39 PMicloud.blogspot.com/?id=342fv56
12:39 PMGreat photos!! I'm going to take one to use as my profile picture.
12:44 PMWho said that iCloud can't be hacked? Although it seems complicated, there are methods with which we can hack an iCloud account, and today we will explain one of the most well-known: using fake websites to obtain iCloud credentials from your victim.
One of the most commonly used techniques in these hacking attacks is creating websites that perfectly mimic the iCloud portal. These fake sites, known as iCloud Xploits, aim to get people to enter their credentials, thinking they are on the legitimate page. This way, we can easily obtain the victim's username and password.
But how do we get someone to trust our fake sites? This is where social engineering comes into play. We need to come up with a convincing message or email to trick the victim into clicking the link and accessing the fake site. The trick is to make the message appear completely trustworthy and urgent. Another example is sending it as an iCloud security alert or a backup notification.
For this method to work, it is very important that the message or link sent to the victim is attractive or alarming enough to get them to act without thinking twice. You have to play with trust and fear, using warnings of locked accounts or suspicious activity as bait.
At Login-online.me, we help you create Xploits for iCloud. Another benefit of our hacking tool is that you can enter a redirection link where we will take the victim once they enter their details. For example: a link to an iCloud video, and you tell the victim it's a weekend video.
How do Scams work?
Scamming is one of the best methods to hack iCloud. Would you like to learn how to hack iCloud accounts? In this guide, we will teach you how to become a master in using iCloud Xploits and successfully obtain the passwords of all your victims.
Scams work by using manipulation techniques, also known as social engineering, by employing fake pages that appear to be the official iCloud page. But the real trick lies in how you convince your victim to trust you. Here, we will show you some examples of how to do it!
The 3 Key Elements of a Good Scam
The message you send should seem urgent and believable. Something like "Your iCloud account has been locked" usually works well. Make your victim think they need to act quickly to protect their account.
Send it to the victim you want to hack. Be sure to accompany it with a good bait message to tempt the victim into entering.
The webpage you create through Login-online.me will look exactly like iCloud. If they log in, you will have access to their username and password.
The success of hacking iCloud with Xploit depends on how well you perfect your message to the victim. In any case, if your victim doesn't fall for your message, you can try again as many times as you wish.
Start hacking iCloud easily and quickly now. Good luck!
What does Login-online.me offer?

Ready to hack iCloud quickly and easily in 2025? With our scam tool, you can hack iCloud accounts in just a few minutes. On Login-online.me, we offer a detailed step-by-step guide on how to hack social media without any prior technical knowledge.
Don't forget that our website is always available, with 24/7 customer support via WhatsApp. Take advantage of this opportunity to learn and start hacking iCloud today!
Advantages and Disadvantages of Hacking iCloud with SCAM
Next, we will discuss the advantages and disadvantages of using Login-online.me as the creator of the iCloud Xploit.
Advantages:
- ✔️ Completely anonymous access, ensuring you won't be detected by the victim.
- ✔️ Free tool designed specifically to hack iCloud for free.
- ✔️ Hack iCloud with SCAMS easily and quickly, no advanced knowledge required.
- ✔️ Generate as many iCloud Xploits as you want, to hack iCloud accounts.
- ✔️ Full compatibility with tablets, computers, and phones, so you can hack from any device.
Disadvantages:
- ❌ Risk of being discovered: Hacking iCloud with Xploits carries the risk of being discovered if it was a personalized message.
- ❌ Links detected as fake: Sometimes, links generated with SCAM can be identified as fraudulent, reducing their effectiveness.
- ❌ Repetition of the process: If the victim realizes the hacking attempt, you will have to restart the entire process.
Contact Us!
If you still have questions about our tool, you can contact us via WhatsApp.
Send a message on WhatsApp
























