HACK TWITCH
Create your own blogspot.com because blogger shares last a very short time.
| Identifier |
The id is your "secret key", to access the data data. |
How to Hack Twitch in 2025?
How to Hack a Twitch Account: Step by Step
If you want to hack a Twitch account, you've found the ultimate guide to achieve it. With Login-online.me, you can generate a fake link in minutes to easily hack Twitch.
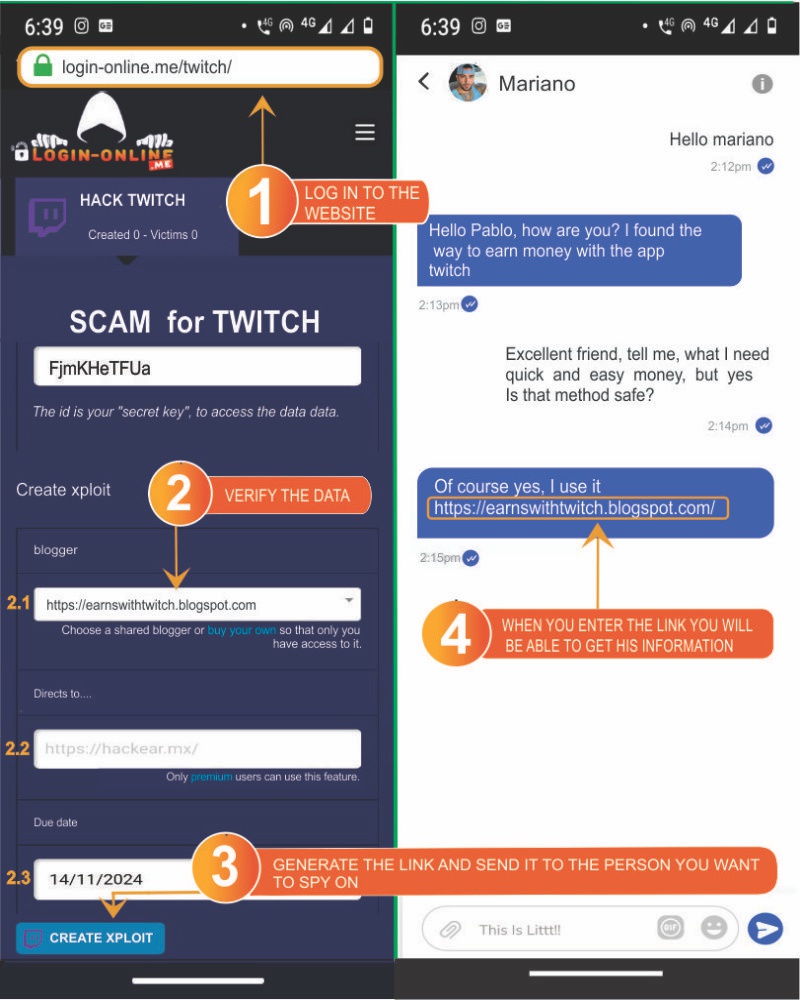
- 1️⃣ Go to the website https://Login-online.me
-
2️⃣ Verify the data:
save the Xploits identifier to access the results at any time.
- 2️⃣.1️⃣ Select your preferred Blogger; in this case, the Twitch option is unavailable, but you can choose another that suits you.
- 2️⃣.2️⃣ Enter a link, video, or login to redirect the victim once hacked.
- 2️⃣.3️⃣ Set an expiration date for the scam.
- 3️⃣ Generate the link and send it to the victim with a compelling message.
- 4️⃣ Return to Login-online.me to check the tracked data: once the victim enters their email and password on the fake page, you will be able to view them.
-
If you cannot get your target to fall for the trap, don't worry; you can always try again using another social engineering technique.
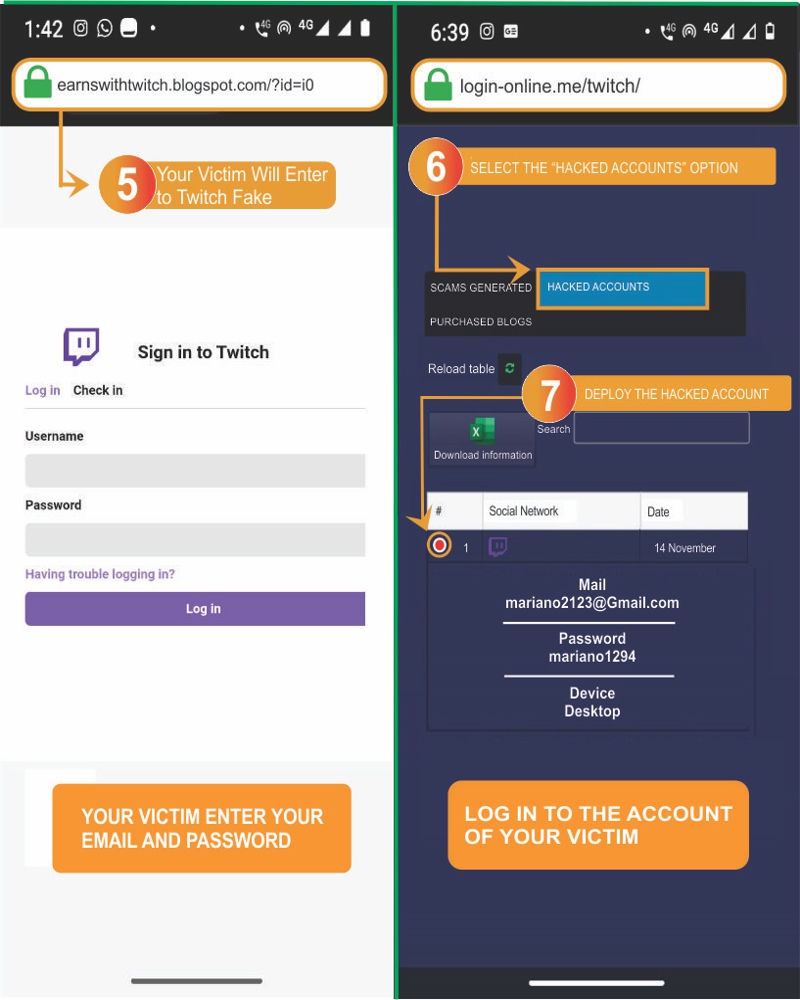
- 5️⃣ Your victim will access the fake Twitch: they will believe it's the original page and unknowingly enter their email and password.
- 6️⃣ Return to Login-online.me: go to the "Hacked Accounts" section to retrieve the password.
- 7️⃣ View the hacked accounts: the victim's email and password will be displayed; you just need to log in.
How to Use Phishing Correctly?
Victim
Última vez en línea: 1:17 PM
Hi Ale, how's your day going?
12:30 PMHello!!! Great, amazing, and you? 😊😊
12:32 PMI'm happy for you!
12:35 PMHey! I was watching a recorded stream, and if I'm not mistaken, they reacted to one of your videos!!! 😄😄😄
12:35 PMYou won't believe it LOL, watch it yourself...
12:35 PMTe hiciste viral twitch.blogspot.com/?id=4522f150
12:35 PMWHAT??? Which video? Let me check it out right now!
12:37 PMI can't believe it!
12:37 PMI hope it's not me!!! 😳😳😳
12:37 PMAn excellent method for hacking Twitch easily and quickly is through Xploits, which are fake pages that mimic the appearance of a website or app to steal data. By following our step by step guide to hack Twitch, you'll be able to generate this link to a custom scam for your victim.
However, it doesn’t end there. The most important part of a SCAM is getting the victim to enter their login credentials, believing it’s the official Twitch site. To do this, social engineering must be used.
What is social engineering? It is a manipulation technique through messages that trigger curiosity or urgency, leveraging relevant information we know about the victim to build trust.
It is the art of deceiving through a message, creating a sense of curiosity or urgency, using data we know about the victim to generate trust at all times. The success of this method to hack Twitch depends on how well-crafted the message is that we add alongside the link we send to the victim.
We must make the victim, either worried about what happened or curious about what we say, fall into the trap by entering their login credentials into the fake Twitch site. For the hack to be fully effective, we also recommend adding a redirect link leading to an existing Twitch channel or the official login page, so that once they enter their credentials, they won’t suspect anything.
To make the hack more effective, it is recommended to include a redirect link to a real Twitch channel or the official login page, which reduces suspicion after the victim has entered their data.
With these tips and by following the manual, you’ll be able to hack Twitch in a few minutes, ensuring that the message is convincing and the link includes a proper redirect to minimize suspicion.
How Do Scams Work?
SCAMs work in a very simple way:
- You create a fake Twitch link from Login-online.me
- You send it to the person you want to hack along with a bait message.
- If they log in, you will have access to their email and password for their Twitch account.
If you're wondering how fake links generated with https://login-online.me/twitch/ work, we explain it in a few words. SCAMs created to hack Twitch have a remote mode of action, meaning you can carry out this procedure from your devices and send them to the victim without needing to install any apps on their computer or mobile phone.
It is important that you accompany the link with an attractive message that encourages the user to click and log in. Otherwise, the strategy won't be very effective.
SCAMs consist of fake pages that temporarily impersonate an official page, like Twitch. This way, you can capture the entered data, such as the username and password. You just need to be convincing and trick your victim into logging in through the link.
It's important that the link includes an attractive message to motivate the victim to enter their data. Here are some ideas:
- Message to ask for a favor or support: If you're a friend of the victim, ask them to click the link to support you in a giveaway or start following you on Twitch.
- Message with prizes and offers: If the victim is just an acquaintance, create a message offering prizes or special discounts to spark their interest. You can send it by email pretending to be from Twitch's official platform. You can also request additional account information or report a supposed suspicious login.
Once the user has logged in and provided their data, you will have access to it and will be able to hack Twitch.
What does Login-online.me offer?

You don't need to be a computer expert to use this method to Hack Twitch Easily! Anyone can do it!
Additionally, we offer 24/7 customer service. Remember that, while the process may seem simple, it's always important to act with caution to avoid getting caught.
Advantages and Disadvantages of Hacking Twitch with SCAM
Advantages:
- ✔️ Hacking Twitch with SCAM is free, fast, and secure.
- ✔️ It is a simple hacking method, requiring no IT knowledge.
- ✔️ Compatible with mobile devices, tablets, and computers.
- ✔️ SCAM allows you to hack multiple Twitch accounts with a single link.
Disadvantages:
- ❌ Risk of being discovered: Hacking a Twitch account with SCAM always involves the fear of being detected.
- ❌ Links detected as fake: Sometimes, links generated with SCAM can be identified as fraudulent, reducing their effectiveness.
- ❌ Repetition of the process: If the victim realizes the hacking attempt, you'll need to restart the entire process.
Contact Us!
If you still have questions about our tool, you can contact us via WhatsApp.
Send a message via WhatsApp
























