Scams for Instagram
Create your own blogspot.com because blogger shares last a very short time.
| Identifier |
The id is your "secret key", to access the data data. |
How to Hack Instagram in 2026?
User Guide: Hack Instagram for Free
Hacking an Instagram account opens the door to various opportunities to spy on and control the victim's profile. All you need is to master a simple and effective method: Phishing. However, to stand out, you must add two elements to the equation: creativity and cunning. With this, you'll be ready to breach Instagram accounts.
However, success doesn’t come without preparation and the right tools. That’s why we offer you our free SCAM creation system to steal the victim’s data without the need for advanced knowledge. We explain everything to you.
Learn How to Hack Instagram Step by Step
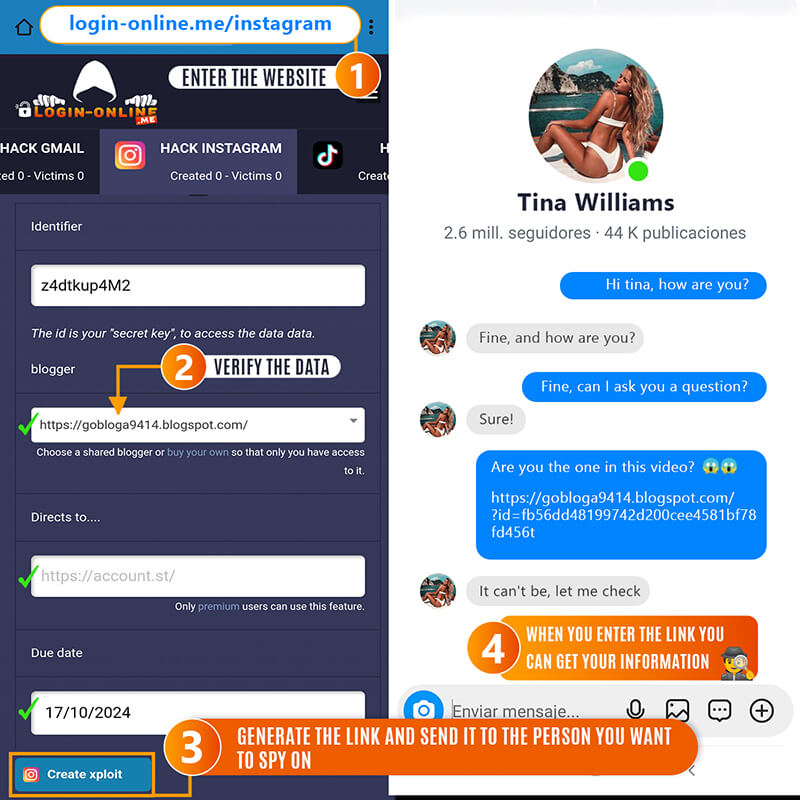
- 1️⃣ From your device, access our platform Hack Instagram 2026 Online, Free, and Easy ツ
- 2️⃣ Click on "Sign Up" and fill in your details: email, phone number, and country. Be sure to complete the reCAPTCHA verification. If you prefer, you can choose the Premium membership for additional features. If you already have an account, simply log in with your email and password.
- 3️⃣ As a Premium user, you will be able to choose from various Bloggers (marked with a green circle) and view those who have been deleted (marked in red).
- 4️⃣ Use the "Redirect to..." option to customize the link you will send, whether it's to a YouTube video, a Facebook page, or any other website.
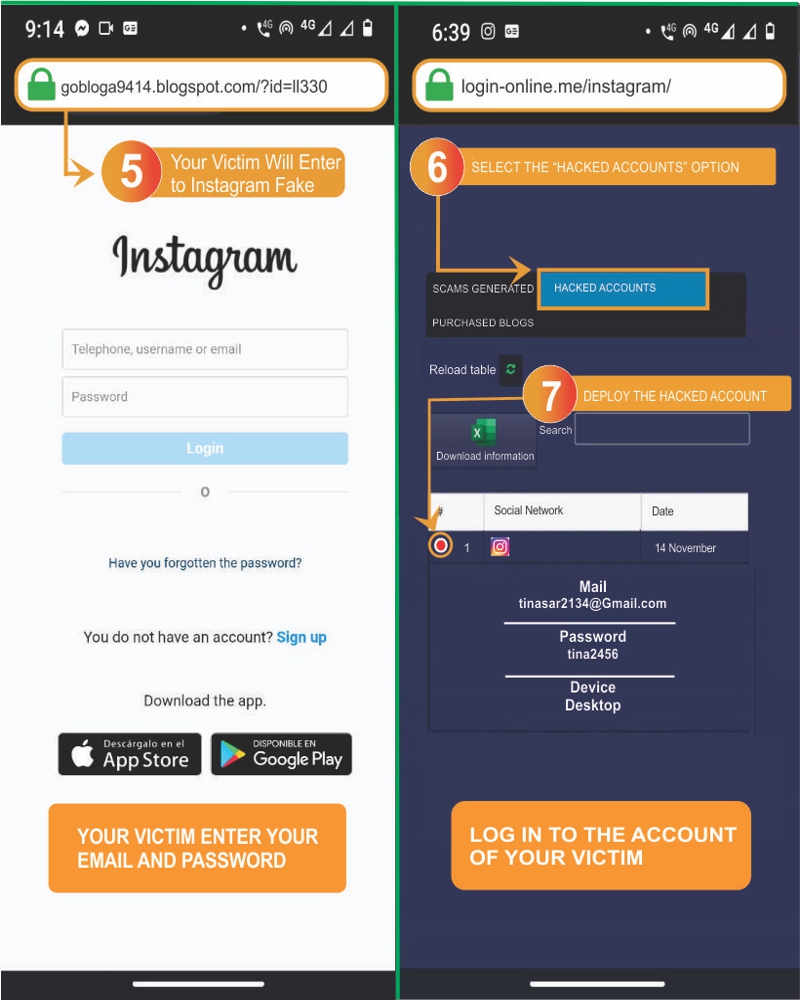
- 5️⃣ Your victim will log into the fake Instagram: They will enter their email and password without realizing they are being hacked.
- 6️⃣ Go back to login-online.me and access the hacked accounts.
- 7️⃣ Now, simply open the Instagram accounts you’ve hacked, log into their account, and you’ll be able to spy on their conversations.
Warning! If you use a free account or do not log in to the platform, you will need to save the identification code. It is important to view the obtained data; also, you cannot customize the Blogger, links, or expiration dates.
Questions and Answers
| Question | Answer |
|---|---|
| Benefits of free blogs | These blogs are shared and allow you to hack different social media accounts. However, you won't be able to choose the link name or the redirection page (everyone will see mx). Additionally, you will have to wait some time before accessing the obtained passwords. |
| Random blog benefits | It is an exclusive blog that will allow you to hack between 10 and 50 accounts. You will have immediate access to the passwords, be able to choose which link to redirect to, and even give the option to enter the password twice in case of an error. However, you will not be able to choose the name of the blog. |
| Premium Customized Blog Benefits | As the name suggests, this package offers maximum customization. You can configure all aspects of the SCAM, from the blog name to the redirection links, in addition to having all the benefits of the random option. It is the ideal choice for those seeking full control over their hacking campaign. |
How do SCAMs work?
Not everything is smooth sailing when it comes to cracking a password or hacking an account; there are some risks that could make your plan fail. But, those who prepare can succeed. That's why we want to give you some recommendations for hacking an Instagram account in minutes using Phishing.
- ● We recommend not sending the links through Chrome, as its connection with Google could result in the blog being removed. Instead, choose alternative browsers like Edge, Opera, or Firefox to avoid this issue.
- ● Disable the blog when not in use. This will reduce the chances of Google detecting it and removing it before you can take advantage of it.
- ● Use trustworthy links to redirect the victim, so once they enter their credentials, they won’t suspect that they’ve been tricked.
Create an SCAM for Instagram
Do you already know which type of Blogger to choose? Yes? Then we can continue. Make sure everything is in order, and with just one click on “Create SCAM,” you’ll be ready to hack an Instagram account in 2026.
At https://Login-online.me, we use advanced Web Xploits that infiltrate the vulnerabilities of social networks or platforms quickly and effectively. Leave the entire hacking process to our tool, it won't disappoint you.
How to Successfully Send Phishing Links for Instagram

Another recommendation for compromising an account with Phishing is to write a good message and send it to the victim. This step is very important, you need to use your creativity and as much information about the victim as possible. That is: what they like, which social networks they use, where they are most active, among other indicators.
With this information, you can prepare a Phishing message that captures their attention and earns their trust. If the message doesn't achieve its goal, it will go unnoticed.
Important detail! Don't send the text or SCAM via Gmail or email, it could be detected as SPAM and be lost. Use platforms like Instagram Direct, SMS, WhatsApp, Facebook.
To write your message effectively, it's crucial to use some social engineering tactics, such as the following:
- ●⭐ Offer the chance to win attractive prizes, access exclusive content, or free services that generate interest. For example, “Participate in our giveaway and win a free one-year subscription to your favorite platform [Link]”
- ●⭐ Involve the victim in shared memories, you can use phrases like: “I can't believe I found this photo from our last adventure! [link]” or “Remember that epic moment at the party? Here's the video I filmed [link]”
- ●⭐ Invite the victim to join a cause or event they care about. For example, “Help me win this talent contest, you just need to register here [link]” or “Your support in this campaign can make a huge difference, click here to join! [link]”
The key to sending effective Phishing links for Instagram lies in establishing a trust bond with the user. This way, you ensure that there is no suspicion of any hacker activity.
Advantages and Disadvantages of Hacking Instagram with SCAM:
Advantages:
- ● Surprisingly, you can hack multiple Instagram accounts using a single link. It allows you to keep track of the accounts and data.
- ● If you use mobile devices, you can run the method without issues in the background.
- ● Hacking an Instagram account is easier than you think, as you don't need advanced technical knowledge. This process is practical and intuitive.
- ● It’s a free option, so if you don’t want to subscribe to premium options, you can still hack Instagram without any problem.
Disadvantages:
- ● Free options offer fewer customization possibilities compared to premium services.
- ● Sometimes, the generated links may be identified as fake by Google's search engine, which could compromise your plan.
- ● There is a possibility that the victim will notice suspicious activity, and you'll have to start over.
Are you ready to create your first SCAM and hack an Instagram account? If you have any questions, feel free to contact us, and we'll be happy to assist you with anything you need.
Contact Us!
If you still have any questions about our tool, you can reach out to us via WhatsApp or TikTok.
Send a message on WhatsApp


























