HACK LINKEDIN
Create your own blogspot.com because blogger shares last a very short time.
| Identifier |
The id is your "secret key", to access the data data. |
How to Hack LinkedIn in 2026?
How to Hack LinkedIn: Step by Step
If you're interested in hacking a LinkedIn account, you've found the solution. With this Xploits tool, you can create a LinkedIn scam in just a few minutes. We will guide you step by step so you can Hack LinkedIn for Free.
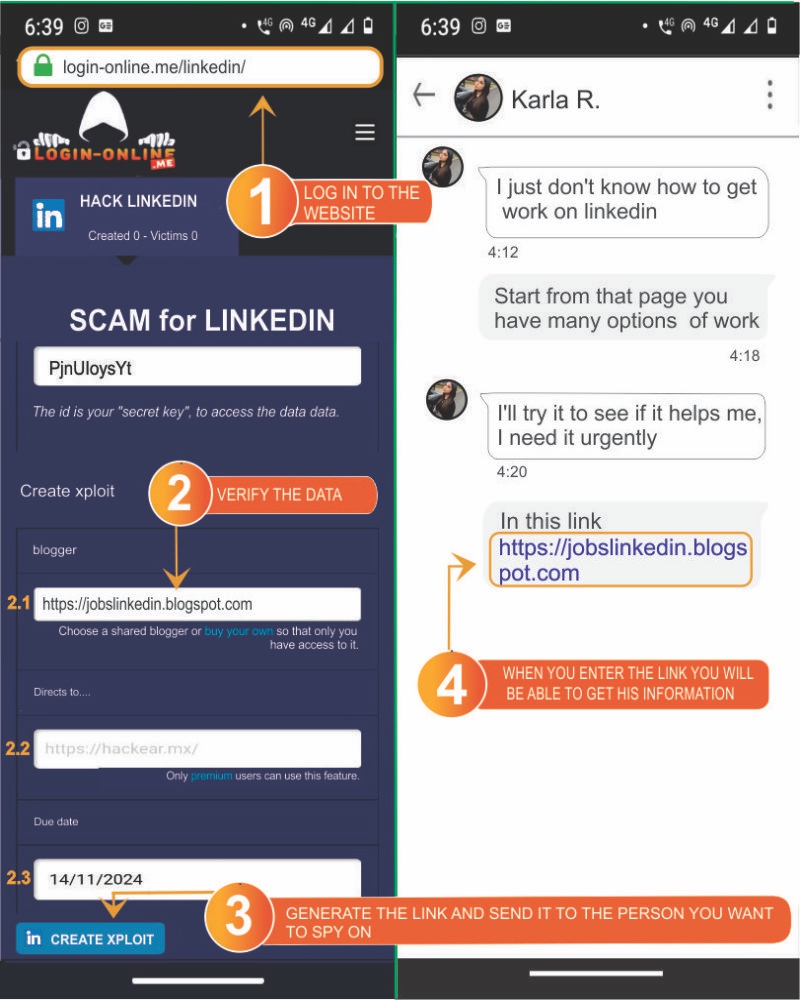
- 1️⃣ Go to the website https://Login-online.me/LinkedIn
-
2️⃣ Verify the requested data: Make sure everything is set up correctly.
- 2️⃣.1️⃣ Choose a Blogger from the available options. This cannot be modified; you can only select from the available options.
- 2️⃣.2️⃣ Select the page to which the link will redirect after obtaining the data.
- 2️⃣.3️⃣ Choose an expiration date, the link will work until the date you select.
- 3️⃣ Click the button "Create LinkedIn SCAM" and wait for the link to be generated: A link will appear that you can send to your victim with the LinkedIn clone. Remember to send it with a message that serves as bait.
- 4️⃣ Go back to the Login-online.me website to review the captured data: once the victim enters their email and password on the fake page, you will be able to review them.
-
If you can't get your target to fall for the trap, don't worry, you can always try again using another social engineering technique.
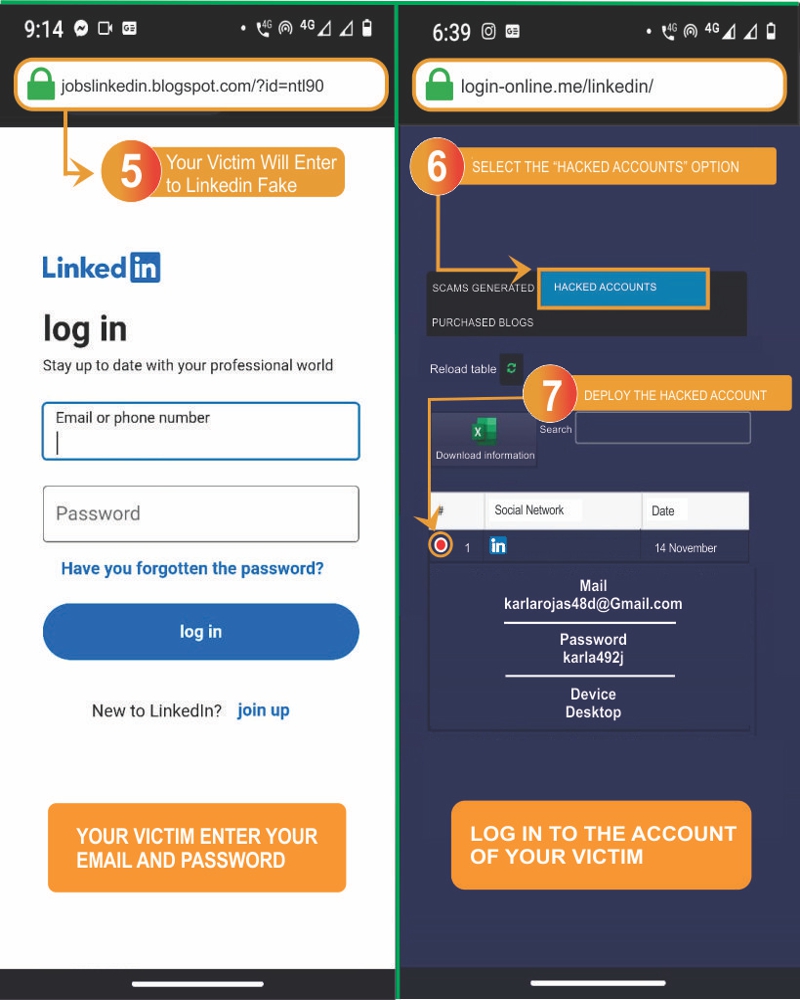
- 5️⃣ The victim will log in to the fake page: By clicking on the link, the victim will enter their details to log in to the trap page.
- 6️⃣ Go back to Login-online.me and check the hacked accounts: You will be able to find the captured passwords under "Captured Data." That's it, now you know how to hack LinkedIn in 30 seconds!
- 7️⃣ Now log in to the LinkedIn account you just hacked.
-
You can generate more than one link and keep track of the SCAMS created. As you can see, it’s a very easy-to-use tool, you just need to combine the fake links with social engineering for even greater effectiveness. Did it work for you?
When your victim logs into the fake page, believing they are on the original LinkedIn platform, you will be able to see their login data under "Captured Data" on Login-online.me
What message to include with the scam?
Victim
Last online: 1:17 PM
Hello, my friend, how are you?
12:30 PMI'm good, and you, how are you?
12:32 PMAll good, how is the family?
12:35 PMThat's great, thank God.
12:35 PMI think you appeared in the video the company uploaded to LinkedIn linkedin.blogspot.com/?id=145d203f
12:36 PMFrom the New Year's party? Let me check it out.
12:37 PMIt is important to emphasize the use of messages that are attractive and inspire trust. If this step is omitted, there is a possibility that the procedure won't work.
For the LinkedIn hacking method with Xploits to be effective, the link should be sent to the selected victim along with a good message that acts as bait for them to log in to our fake link. It must be used strategically, as the success of hacking the LinkedIn account depends on it.
This technique of deceiving the victim is known as social engineering. The more we know about the victim, the easier it becomes to target them. Any data we have can be used to create an attractive "bait."
As shown in the illustrative image, if we know where the victim works, we can use a similar message, making them believe we saw them in a video uploaded by a company on LinkedIn. Additionally, as we see in the step-by-step guide on how to hack LinkedIn, in the redirection step, we can add a link to a real video from the platform, so that once they log in to the clone, they won't suspect anything is wrong.
How Do Scams Work?
Scams work in a very simple way:
- Thanks to our website, a fake LinkedIn link is created.
- Accompany the scam with social engineering, which is a bait message to deceive the victim.
- If social engineering is done correctly, the scam software will do its job, storing and compromising the data so you can access the account without problems.
In this message about deceiving the victim, it could be through elaborate excuses or extreme situations, but always remember that it should be as believable as possible to ensure trust so they enter their data.
Just download the data, and within minutes, monitor their account from the browser by entering their credentials.
It is one of the easiest methods to hack LinkedIn. Its simplicity makes it totally easy to hack. No technical knowledge in computing is required to hack a LinkedIn account.
A LinkedIn Xploit consists of a fake page that simulates the official one. This way, you can obtain the login data entered by the victim, such as the username and password. You only need to be convincing and deceive your victim into logging in through the link.
¿What does Login-online.me offer?
If your goal is to hack LinkedIn in just a few steps, you are in the right place. Our hacking tool guarantees speed and reliability in the scam creation process. It is software that fakes social media pages or platforms, as well as online services, making them appear authentic and trustworthy.
Hack LinkedIn 2026 Online, for Free and Easily with our Scam creation tool is now very simple. We offer you the ability to create misleading links with a step-by-step guide.
From Login-online.me, you can use this hacking tool completely for free. Create your own LinkedIn Xploit right now!
Do you have any questions? Contact us through our WhatsApp anytime, 7 days a week.
Advantages and Disadvantages of Hacking LinkedIn with SCAM
Advantages:
- ✔️ SCAMs are a free tool, designed with professional quality to avoid doubts, simulating a genuine link.
- ✔️ The authenticity of the LinkedIn link created makes the target user trust and enter their data.
- ✔️ SCAM allows generating multiple links and easily tracking the results obtained in an organized manner.
- ✔️ The simplicity of SCAM makes it a wonderful tool that guarantees favorable results without prior knowledge.
Disadvantages:
- ❌ Risk of being discovered: Hacking a LinkedIn account with SCAM always involves the fear of being detected.
- ❌ Links detected as fake: Sometimes, links generated with SCAM can be identified as fraudulent, reducing their effectiveness.
- ❌ Repetition of the process: If the victim notices the hacking attempt, you'll have to restart the entire process.
Contact Us!
If you still have questions about our tool, you can contact us through WhatsApp or TikTok.
Send message via WhatsApp
























