HACK SPOTIFY
Create your own blogspot.com because blogger shares last a very short time.
| Identifier |
The id is your "secret key", to access the data data. |
How to Hack Spotify 2026
The desire to hack Spotify grows every day, and many people are often unsuccessful in doing so. Therefore, we present a very effective tool to hack Spotify for free. Learn about SCAMs.
How to Hack a Spotify Account: Step by Step
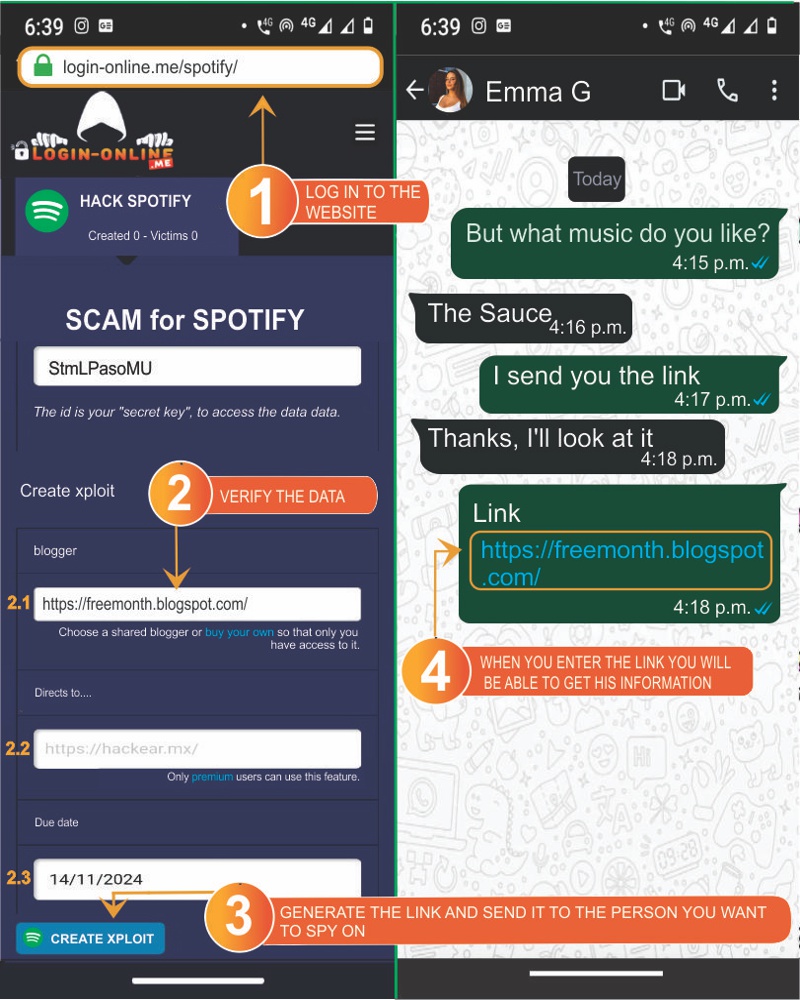
- 1️⃣ Access the website https://Login-online.me
- 2️⃣ Verify the requested data: Copy the scam identifier. You will use it to access the captured passwords.
Each scam you create will have a unique identifier unless you log in or register on the website. We recommend doing so to avoid losing the code and, consequently, the passwords of your victims.
- 2️⃣.1️⃣ Select a Blogger from the available options. This cannot be modified; you can only choose from the available choices.
- 2️⃣.2️⃣ Enter the link of a website to show (e.g., Google) to your victim once they enter their data so they do not suspect anything.
- 2️⃣.3️⃣ Choose an expiration date. The link will work until the day you select.
- 3️⃣ Click on "Create Spotify Xploit" and wait for the link to be generated.
- 4️⃣ Send it to the people you wish to hack and wait patiently.
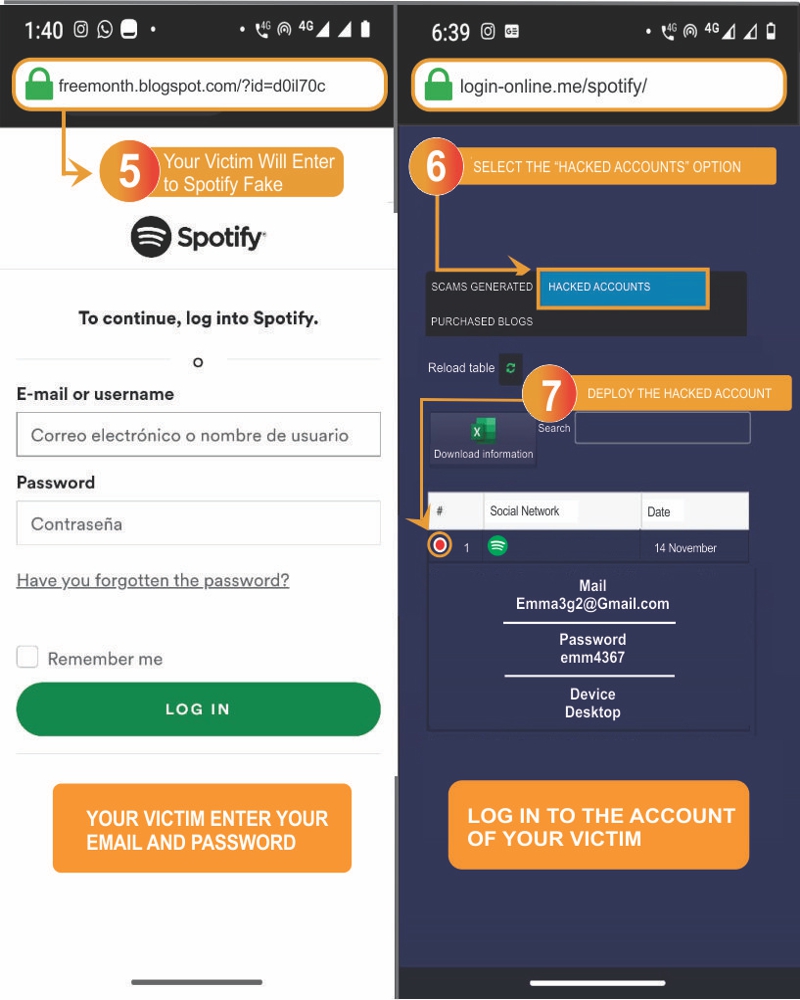
- 5️⃣ The victim will log in to the fake page: By clicking the link, the victim will enter their details to log in to the phishing page.
- 6️⃣ You will find the captured passwords in "Hacked Accounts". Now you know how to hack Spotify in 30 seconds!
- 7️⃣ Hacked Account: Now access the Spotify account you just hacked and start playing music.
If you don't manage to get your target to fall into the trap, don't worry, you can always try again using another social engineering technique.
Send the generated link to the victim
Victim
Última vez en línea: 3:24 PM
Hello beautiful! How are you? 😘
12:30 PMHello handsome! I'm good, and you?
12:32 PMVery well!
12:35 PMHey, have you seen Bad Bunny's new album??? It's awesome!!! You should listen to it, no one else has it 😈♥️♥️🔥
12:35 PM😱😱😱 spotify.blogspot.com/?id=4522f150
12:35 PMWoww!!! I didn't know that 😱
12:37 PMI'm going crazy, I'm a fan! Let me log in and I'll listen to it right away 🔥🔥
12:37 PMXploits are an effective method as long as they are accompanied by social engineering, and the best part is that you don't need to be an expert in computer science to use Xploits to Hack Spotify.
You need to gain the victim's trust so they click on the link we will send. It is recommended to send a trustworthy message to avoid the victim identifying the link as a virus or harmful. This may be one of the more complex points of the method, but if you succeed, you'll be able to hack a Spotify account.
You need to be creative with any information you know about the victim, like their favorite genre or music group, and talk to them about an exclusive song they can listen to through the link. You can also impersonate Spotify, asking for additional account information or notifying them of a supposed suspicious login.
If everything goes well, in less than a minute, you will be able to get the data to log in and hack a Spotify account for free. One of the advantages of this method is that it makes it easy to create different SCAMs.
How do Scams work?
Scams work in a very simple way:
- Create a fake Spotify link from Login-online.me.
- Send it to the person you want to hack to get them to log in. Remember to include a good bait message so it seems trustworthy.
- If they log in, you'll have access to their username and password.
Spotify Xploits are a common and reliable hacking method. Their effectiveness lies in the social engineering technique we use to deceive the victim into clicking our fake link.

We can use different strategies and technologies to carry out our deception. The key is to be creative with any personal information we have about the victim.
An Xploit is a fake login page that allows us to hack a Spotify account. The most important thing is our message, which serves as the bait to get the victim to log in so we can access their data.
The most common social engineering techniques to hack Spotify are:
Personalized message: By knowing the victim, we can create a personalized message, talking about an album release they can listen to by clicking the link we send, or an exclusive podcast.
Platform message: We can contact the victim via email, pretending to be the official platform, requesting additional account information or informing them of a supposed suspicious login.

What does Login-online.me offer?

Hack Spotify 2026 Online, Free, and Easy using our tool to create Xploits is very quick.
You can use Login-online.me 24/7. We also offer customer service 24/7 via WhatsApp. Start hacking Spotify right now!
At Login-online.me, we have three different plans:
- Free: This is a shared blog to hack different social media accounts, but without options to choose the name, the website to redirect (users will see mx), and you must wait to see the passwords.
- Premium Random: For $10 USD, you get access to a blog for yourself with the ability to hack 10 to 50 accounts. You can also view the passwords automatically, choose the redirection link, and enter data twice. However, you cannot choose the blog name.
- Premium Customized: This allows you to customize all the SCAM creation options and enjoy all the previously mentioned features. Unlike the “Random” option, you can choose the blog name from 3 customized blogs. This service costs $20.
Advantages and Disadvantages of Hacking Spotify with SCAM
Advantages:
- ✔️ You quickly and freely obtain information such as passwords, usernames, and emails.
- ✔️ No prior knowledge of technology or computer science is needed to use this tool; it's easy to use.
- ✔️ Allows you to create a large number of SCAMs and manage them in an organized way, monitoring the generated data.
- ✔️ It's a very reliable method for breaching social media systems or platforms like Spotify to gain access to accounts.
Disadvantages:
- ❌ If the SCAM isn't accompanied by a convincing message that builds trust, the victim may discover the hacker.
- ❌ There are instances when the browser detects the link as fake, which can lead to discovery.
- ❌ Process repetition: If the victim realizes the hack attempt, you'll have to restart the entire process.
Contact Us!
If you still have questions about our tool, you can contact us via WhatsApp or TikTok.
Send Message via WhatsApp
























